FFIEC Cybersecurity Assessment Tool 2015-2025 free printable template
Show details
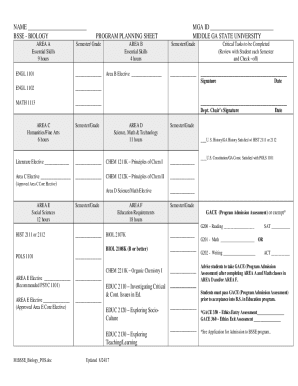
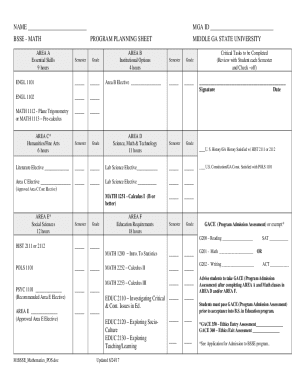
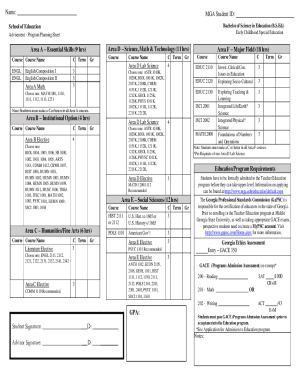
Risk-based approach to managing cybersecurity risk p. Mapping Cybersecurity Assessment Tool D1. RM. A mapping is available in Appendix B Mapping Cybersecurity Assessment Tool to the NIST Cybersecurity Framework. FFIEC Cybersecurity Assessment Tool Overview for Chief Executive Officers and Boards of Directors In light of the increasing volume and sophistication of cyber threats the Federal Financial Institutions Examination Council 1 FFIEC developed the Cybersecurity Assessment Tool Assessment...
pdfFiller is not affiliated with any government organization
Get, Create, Make and Sign ffiec cybersecurity tool form
Edit your ffiec overview form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your ffiec assessment form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit ffiec cybersecurity assessment tool pdf online
Use the instructions below to start using our professional PDF editor:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit ffiec cybersecurity assessment tool form. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
With pdfFiller, dealing with documents is always straightforward.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out ffiec tool get form
How to fill out FFIEC Cybersecurity Assessment Tool
01
Begin by gathering your organization's cybersecurity policies and procedures.
02
Access the FFIEC Cybersecurity Assessment Tool on the FFIEC website.
03
Start with the 'Inherent Risk Profile' section to assess your organization's risk levels across various domains.
04
Evaluate the responses in the 'Cybersecurity Maturity' section based on your current capabilities.
05
Use the tool's interactive features to compare your Inherent Risk Profile with your Cybersecurity Maturity.
06
Document findings and identify areas for improvement.
07
Create an action plan based on the results of the assessment and implement necessary changes.
Who needs FFIEC Cybersecurity Assessment Tool?
01
Financial institutions such as banks, credit unions, and other entities regulated by the FFIEC.
02
Operational risk and compliance teams within these institutions.
03
Cybersecurity professionals responsible for risk management and policy enforcement.
04
Management and board members seeking to understand their organization's cybersecurity posture.
Fill
ffiec cybersecurity assessment
: Try Risk Free






People Also Ask about who is required to file ffiec cybersecurity encouraged to use the cybersecurity assessment tool
What is the cyber security assessment tool?
CSET is a desktop software tool that guides asset owners and operators through a step-by-step process to evaluate industrial control system (ICS) and information technology (IT) network security practices.
What is the best cybersecurity assessment?
NIST Cybersecurity Framework While compliance is voluntary, NIST has become the gold standard for assessing cybersecurity maturity, identifying security gaps, and meeting cybersecurity regulations.
What are types of cybersecurity assessments?
What Are The Types Of Security Testing? Vulnerability Scanning. Security Scanning. Penetration Testing. Security Audit/ Review. Ethical Hacking. Risk Assessment. Posture Assessment. Authentication.
What is the best cybersecurity risk assessment?
10 Best Cybersecurity Risk Management Tools 2023 Cloud GRC. Pathlock. Resolver Risk Management Software. Risk Management Studio. CheckIt. CURA Enterprise Risk Management. Enablon. Isometrix.
How do you write a security assessment?
A security assessment report should include an executive summary, an assessment overview, and a section with results and risk management recommendations. The executive summary provides an overview of the findings and a snapshot of how the company's systems security held up against scrutiny.
How do I prepare for a cyber security assessment?
Hence you need cross-functional input. Step 1: Catalog Information Assets. Your risk management team should catalog all your business's information assets. Step 2: Assess the Risk. Step 3: Analyze the Risk. Step 4: Set Security Controls. Step 5: Monitor and Review Effectiveness.
How do you write a cybersecurity assessment report?
Conducting a Risk Assessment Step 1: Pick a cyber security framework. Step 2: Identify cyber business risks. Step 3: Choose controls from cyber security framework. Step 4: Create a checklist. Identify data & technology assets. Step 6: Assess controls on data & technology assets. Step 7: Quantify or qualify risk.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I edit ffiec cybersecurity assessment tool download on a smartphone?
The pdfFiller apps for iOS and Android smartphones are available in the Apple Store and Google Play Store. You may also get the program at https://edit-pdf-ios-android.pdffiller.com/. Open the web app, sign in, and start editing cybersecurity vulnerability assessment form.
Can I edit ffiec cybersecurity assessment tool xls on an iOS device?
Create, modify, and share ffiec cybersecurity assessment tool excel template using the pdfFiller iOS app. Easy to install from the Apple Store. You may sign up for a free trial and then purchase a membership.
How do I complete ffiec cybersecurity framework on an Android device?
On an Android device, use the pdfFiller mobile app to finish your ffiec cybersecurity. The program allows you to execute all necessary document management operations, such as adding, editing, and removing text, signing, annotating, and more. You only need a smartphone and an internet connection.
What is FFIEC Cybersecurity Assessment Tool?
The FFIEC Cybersecurity Assessment Tool is a framework designed to help financial institutions identify their cybersecurity risks and assess their preparedness against those risks.
Who is required to file FFIEC Cybersecurity Assessment Tool?
All financial institutions that fall under the supervision of the FFIEC members, including banks, credit unions, and other regulated entities, are encouraged to use the Cybersecurity Assessment Tool.
How to fill out FFIEC Cybersecurity Assessment Tool?
To fill out the FFIEC Cybersecurity Assessment Tool, institutions should evaluate their cybersecurity risks, assess their maturity level in various domains, and complete the assessment by answering a series of guided questions designed to gauge their threat and vulnerability landscape.
What is the purpose of FFIEC Cybersecurity Assessment Tool?
The purpose of the FFIEC Cybersecurity Assessment Tool is to establish a standard approach for financial institutions to evaluate their cybersecurity posture, identify risks, and encourage effective risk management practices.
What information must be reported on FFIEC Cybersecurity Assessment Tool?
The information reported on the FFIEC Cybersecurity Assessment Tool includes the institution's risk profile, maturity level in various cybersecurity domains, and any identified vulnerabilities or areas for improvement.
Fill out your FFIEC Cybersecurity Assessment Tool online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cybersecurity Assessment Tool Ffiec is not the form you're looking for?Search for another form here.
Keywords relevant to cybersecurity assessment tool excel
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.